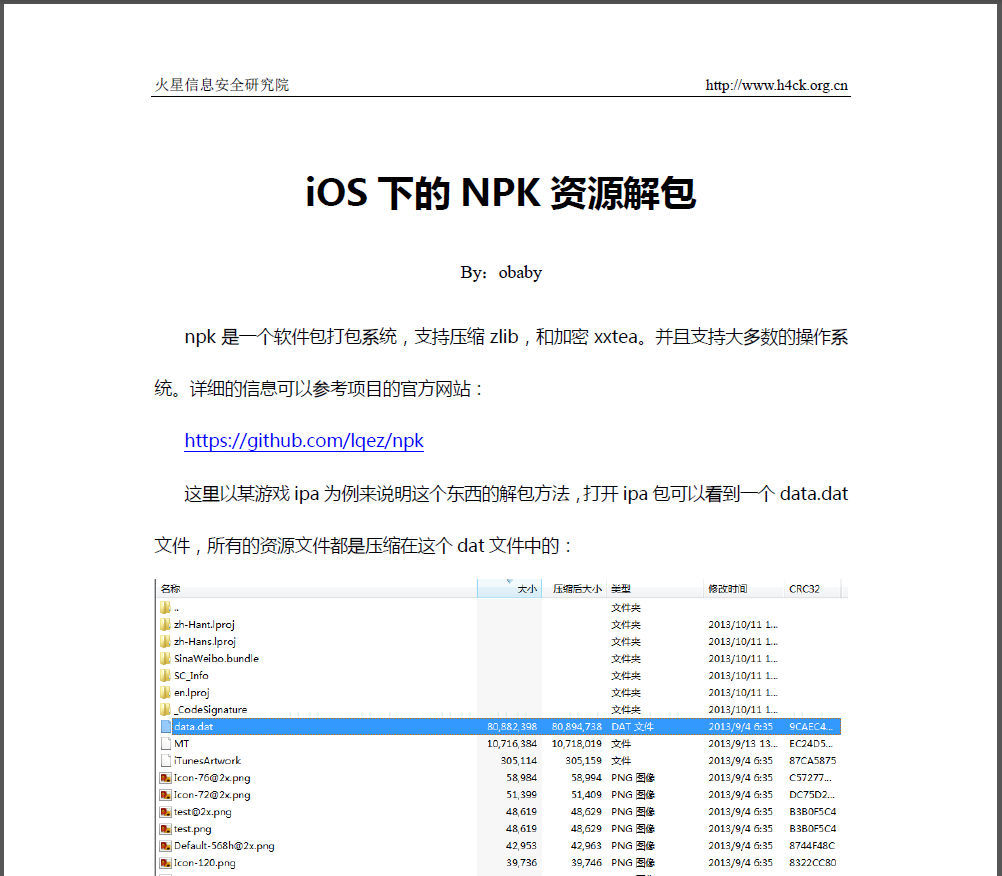
PDF下载链接:http://bbs.pediy.com/attachment.php?attachmentid=83753&d=1382016529
An IDA plugin to graph all paths between two functions
a plugin to find all code paths between two functions. This can significantly narrow down the number of paths that require investigation
插件地址:https://code.google.com/p/idapathfinder
原文链接:http://www.devttys0.com/2013/04/finding-all-paths-between-two-functions-in-ida/
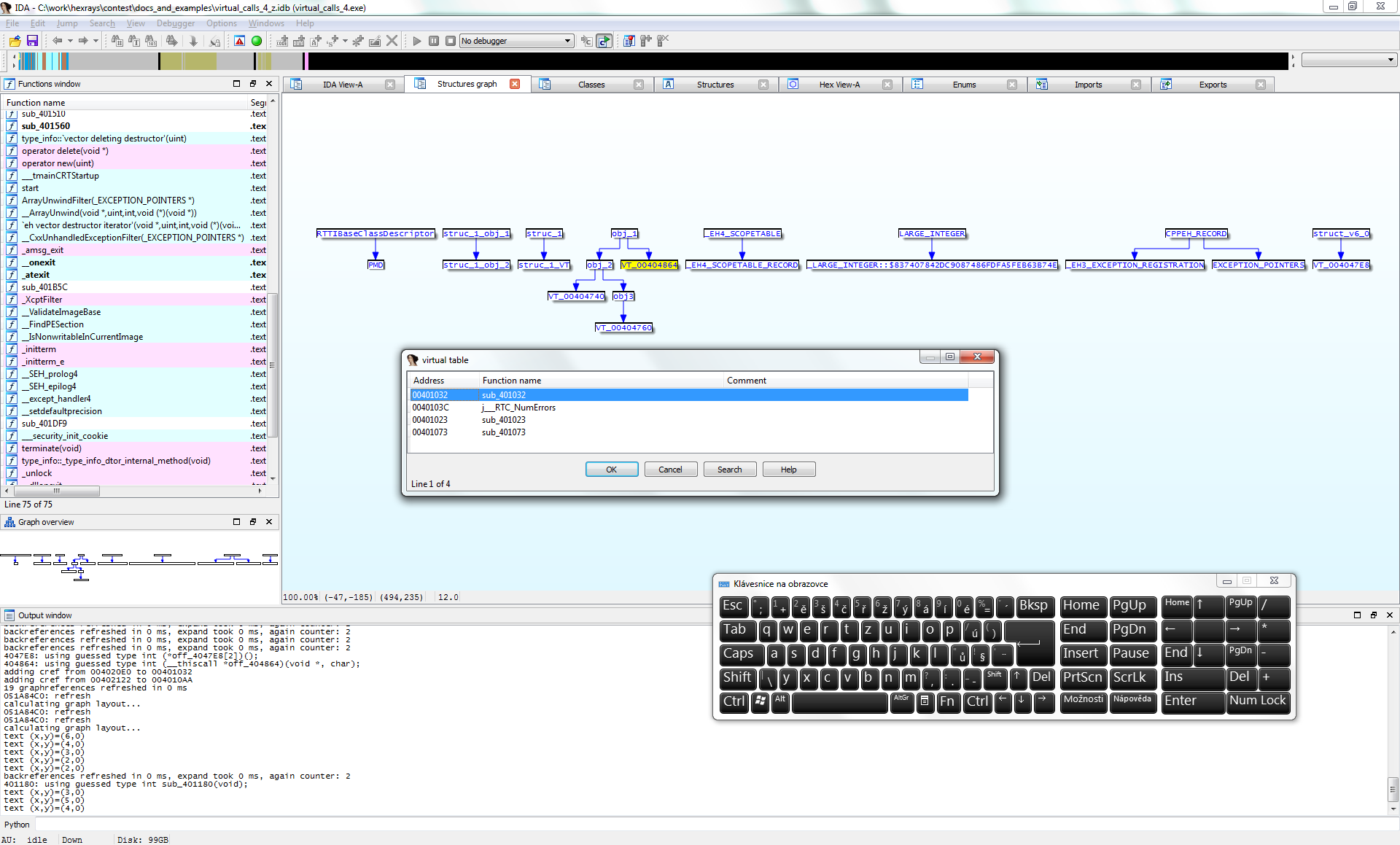
hexrays_tools&CrowdDetox Rebuild for IDA 6.x
Milan’s useful functions for Hex-Rays decompiler
================================================
New hexrays features:
Assist in creation of new structure definitions / virtual calls detection
===========================================================================
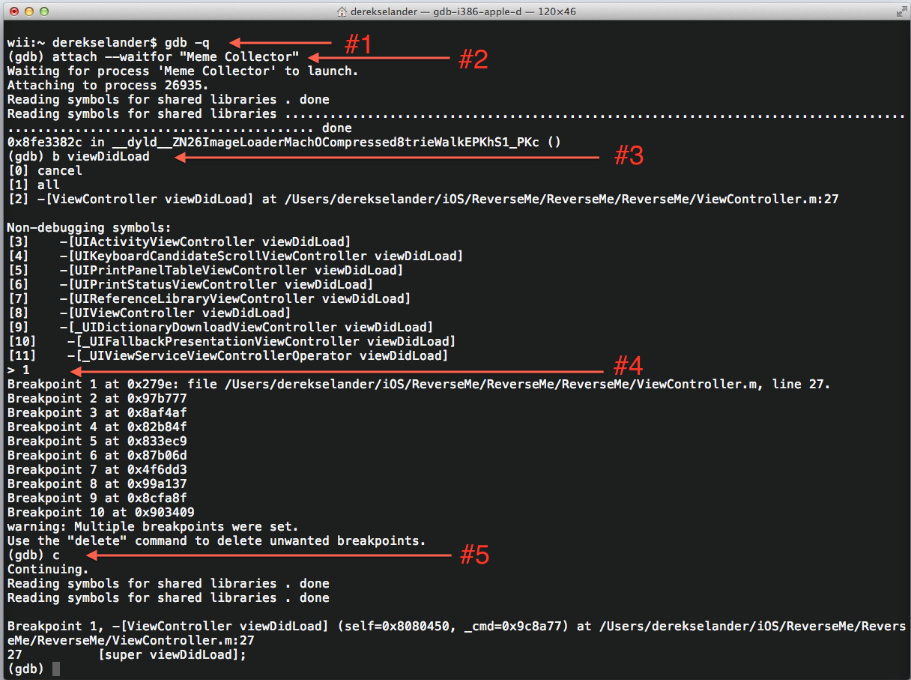
【翻译】iOS 应用安全以及分析
文章内容较多,详情请下载附件进行阅读~
第一部分:http://bbs.pediy.com/showthread.php?p=1225773#post1225773
第二部分:http://bbs.pediy.com/showthread.php?p=1226452#post1226452