更新了一下Unicode字符串识别插件,去掉了非PE格式下不能加载插件的限制。上图为MachO文件格式。
Nanomite – Graphical Debugger for x64 and x86 on Windows
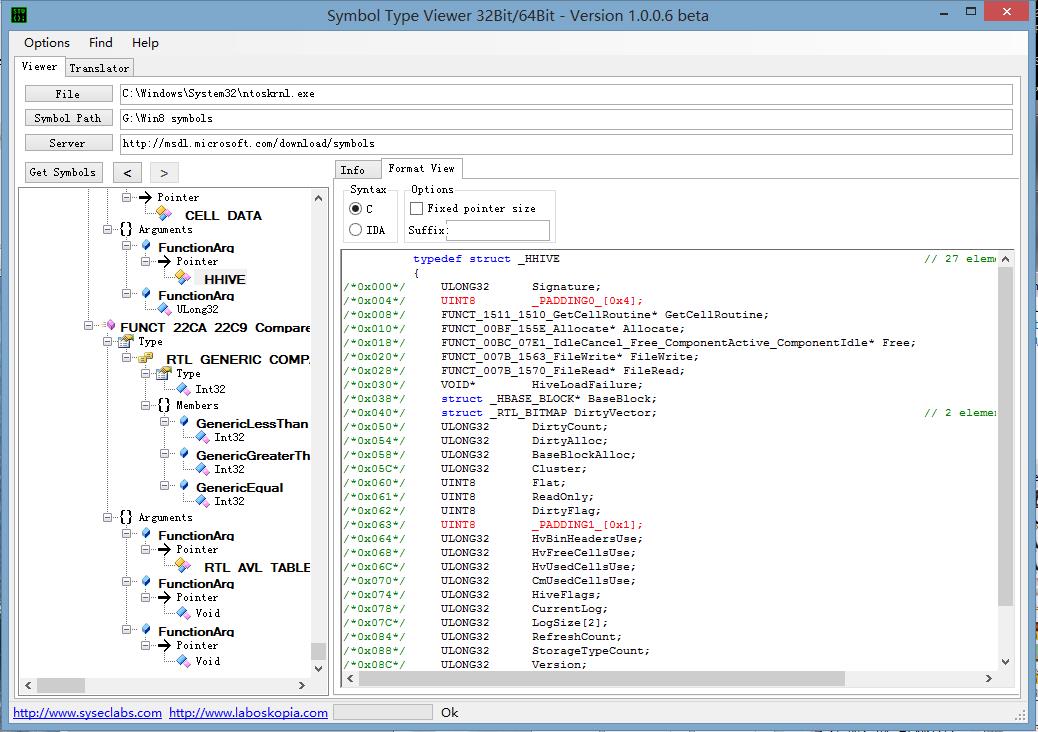
Symbol Type Viewer 1.0.0.6
Symbol Type Viewer is a tool which makes it possible to easily visualize the types which can be defined in the symbols of the modules of the systems Microsoft Windows 32/64bit. Moreover, it makes it possible to convert these informations for the C language (.h) and the disassembler IDA of DataRescue (.idc).
ImpREC lite v11 Source Code(Share)
News:
—–
ImpREC is back to public. This version can now support Windows 95 (Thanks to EliCZ,
Unknown One and ZigD for testing).
It has also been redesigned to support more import rebuilding schemes (relative calls for
example). The plugin interface has changed completely (using filemapping) and now supports
the ‘Exact Call’ feature. This last one has been linked with the ‘Create New IAT’. It will
be useful for all mangled schemes which annihilate completely or partially the IAT. The
‘AutoTrace’ is more stable because it will not use the Tracer Level2 anymore. A built-in
coloured disassembler/hew-viewer will help you to watch the redirected code. Then you
should not need the ASProtect plugin because of no more updates but it still is there as
example. Please take a look at <History.txt> for all details.I hope you will enjoy this version like i did to make it,
Regards,MackT/uCF.
v1.6 FINAL (PUBLIC VERSION)
—————————
– Misc
– Finally fixed the bug in the check for adding section (Thanks to Christoph)
v1.6 beta *PRIVATE*
——————-
– Tracers
– Tracer Level3
– Added EIP Log
– Misc
– Finally, support relative calls rebuild (not with the loader yet)
– Added a disassembler window for redirected code
– Added colour to all known imports (Thanks to Jeff Schering)
– Added a hex viewer (built with the disassembler)
– Fixed blink in RichEdit control
– Checkbox “OpCodes” is enable/disable depending on “Hex View”
(Thanks to Muffin)